How To Do Threat Hunting with Falcon Identity Protection
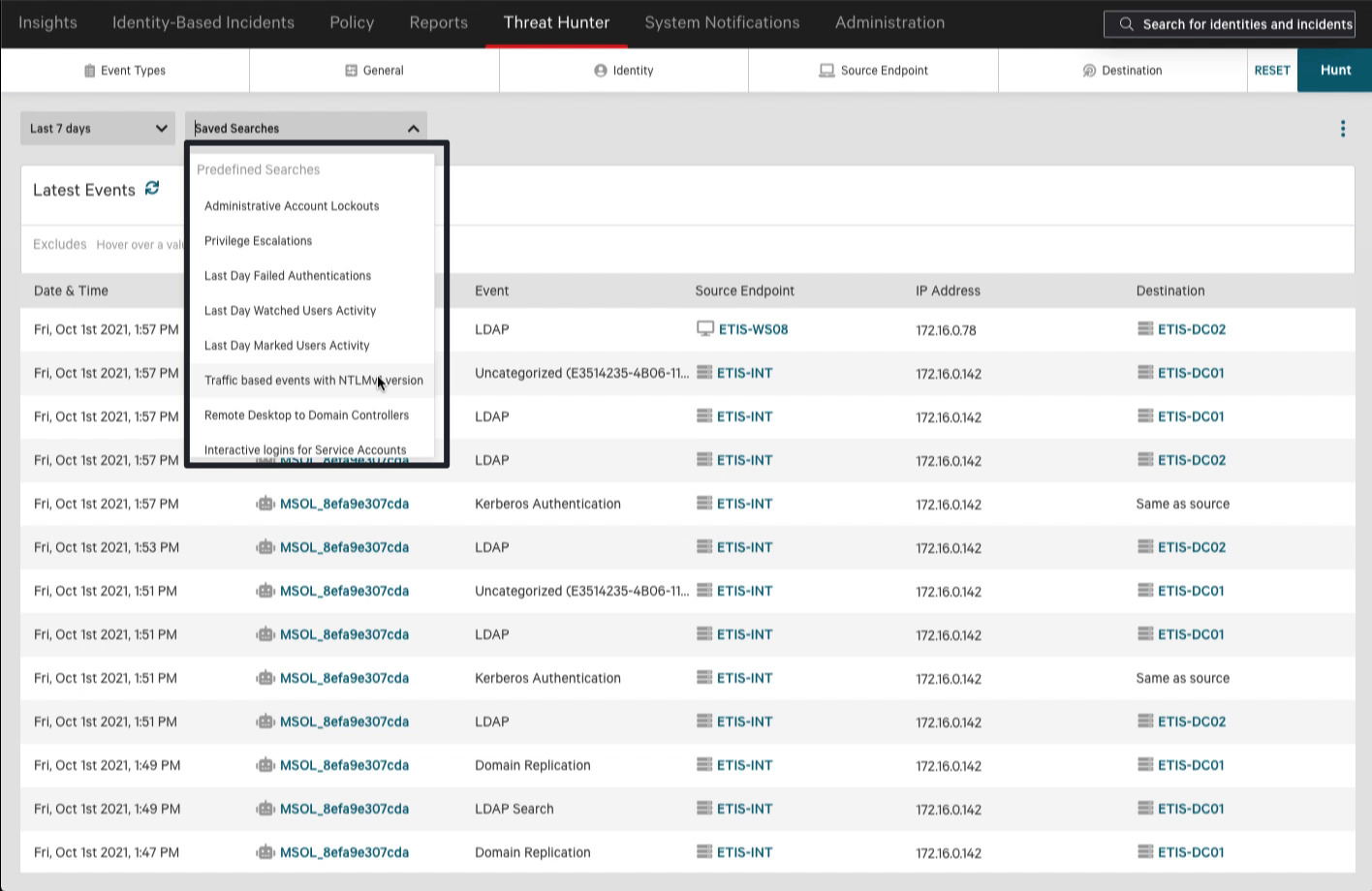
This video illustrates how to use CrowdStrike Falcon® Identity Protection to proactively hunt for identity-based threats including suspicious lateral movement, domain replication, credential scanning etc before they can escalate to an attack.
Discover More at our
Resource Center
TECHNICAL CENTER
For technical information on installation, policy configuration and more, please visit the CrowdStrike Tech Center.
Visit the Tech Center