What is managed XDR (MXDR)?
Managed XDR (MXDR), sometimes referred to as XDR as a service or XDRaaS, is a holistic security service that provides advanced detection and response capabilities using a combination of digital technologies and outsourced human-led expertise. It is considered a transformative approach to cybersecurity because it addresses limitations posed by traditional security models and provides protection across security sources like email, cloud servers, and networks.
Building on the existing capabilities of Managed Detection and Response (MDR) and Extended Detection and Response (XDR), MXDR combines both human expertise and the latest digital tools to enable robust data collection and correlation capabilities, as well as continuous threat hunting, threat monitoring and incident response — all delivered as a service.

2023 Threat Hunting Report
In the 2023 Threat Hunting Report, CrowdStrike’s Counter Adversary Operations team exposes the latest adversary tradecraft and provides knowledge and insights to help stop breaches.
Download NowMDR vs. MXDR
To understand the difference between MDR and MXDR it may be helpful to first review the difference between EDR and XDR.
| EDR | XDR |
|---|---|
| EDR is the baseline monitoring and threat detection tool for endpoints and the foundation for every cybersecurity strategy. This solution relies on software agents or sensors installed on endpoints to capture data, which it sends to a centralized repository for analysis. | XDR extends EDR capabilities to protect more than endpoints. The XDR solution “extends” across the infrastructure, streamlining security data ingestion, analysis, and workflows across an organization’s entire security stack to enhance visibility around hidden and advanced threats, and to unify the response. |
Essentially the difference between MDR and MXDR is the same as the difference between a traditional EDR and next-gent XDR tool — except that both MDR and MXDR are delivered as a service.
| MDR | MXDR |
|---|---|
| MDR is essentially EDR purchased as a service. This service manages endpoint security and focuses on mitigating, eliminating and remediating threats with a dedicated, experienced security team. | MXDR is XDR purchased as a service. It provides the same capabilities as an XDR capability delivered by an external team that acts as a seamless extension of the internal IT and security team. An MXDR service from a reputable vendor is considered to be the highest standard of protection available on the market today. |
How does MXDR work?
MXDR combines the above technologies, tools, solutions and human-led services into a single managed service. This enables complete, end-to-end visibility across the entire attack surface and allows the service provider to enable 24/7 monitoring, detection, investigation, and prioritization of any alerts surfaced by the combined solution set.
MXDR will also automate some aspects of the response and remediation activity, particularly for alerts that pose little risk or can be resolved easily. For more complex or higher-risk threats, the system will engage a team of response agents to help the organization rapidly develop and execute a response plan to remediate the incident.
MXDR components and capabilities
MXDR combines advanced technology and services into a single, cohesive offering.
In most instances, the MXDR service provider consolidates all activity, data and insights from the extended security toolset and team into a Security Operations Center (SOC), a centralized security function that enables security experts to continuously monitor, detect, analyze, respond to, and report security incidents.
Key security capabilities within MXDR include:
- Prioritization: MXDR automates detection alerts and applies pre-determined rules to help security teams distinguish between benign events or false positives and true threats. The system then distills this information into actionable insights for the security team, enabling them to prioritize activity.
- Threat intelligence: Threat intelligence is data that is collected, processed, and analyzed to understand a threat actor’s motives, targets, and attack behaviors. Threat intelligence enables security teams to make faster, more informed, data-backed security decisions and change their behavior from reactive to proactive in the fight against threat actors.
- Continuous threat detection: Threat detection is the process of analyzing a security ecosystem at the holistic level to find malicious users, abnormal activity and anything that could compromise a network. Highly evasive cyber threats are the main focus of threat detection and response tools. The most advanced XDR/MXDR solutions protect the organization from both known and unknown threats (attack vectors whose signature is cataloged in various tools’ databases and signatureless files, respectively).
- Vulnerability management: Vulnerability management is the ongoing, regular process of identifying, assessing, reporting on, managing, and remediating cyber vulnerabilities across endpoints, workloads, and systems. An advanced MXDR solution includes a vulnerability management program that uses threat intelligence and knowledge of IT and business operations to prioritize risks and address vulnerabilities as quickly as possible.
- Threat hunting: Threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Cyber threat hunters dig deep to find malicious actors in your environment that have slipped past your initial endpoint security defenses.
- Guided response: Guided response delivers actionable advice on the best way to contain and remediate a specific threat. Organizations are advised on activities as fundamental as whether to isolate a system from the network to the most sophisticated, such as how to eliminate a threat or recover from an attack on a step-by-step basis.
- Remediation: Managed remediation restores systems to their pre-attack state by removing malware, cleaning the registry, ejecting intruders, and removing persistence mechanisms. Managed remediation ensures that the network is returned to a known good state and further compromise is prevented.
- Cyber forensics: Cyber forensics is a service offered by cybersecurity vendors that leverages advanced technologies and data tooling to reconstruct past events and trace the chain of actions to the point of compromise. This not only helps the organization identify how a breach occurred (which can help it improve security measures for the future) but also may shed light on who is responsible for the attack and what their motivations may be.
Learn More
Read this blog to learn how organizations benefit from the implementation, management, response and end-to-end remediation of advanced threats across attack surfaces with MXDR. Solving the Cybersecurity Skills Gap with Managed XDR
5 Benefits of MXDR
1. Reduced complexity and increased efficiency
The threat landscape — and corresponding solution set — has become far more vast and complex for organizations in recent years. Managing the massive numbers of alerts from these security technologies, as well as protecting a huge influx in IoT-enabled endpoints stemming from technology advances and the rise in remote work, makes it far more difficult, complicated, and time consuming for IT teams to protect the entire attack surface and investigate incidents that can arise at any time in any place.
MXDR outsources critical activity like alert monitoring, prioritization and response to an external team, thus freeing up the internal IT team to focus on operations. MXDR also leverages best-in-class technologies and solutions to automate some aspects of threat detection and response, which helps simplify and streamline security activity and enables important efficiency gains for the extended security team.
2. Reduced costs
Though MXDR is a managed service and, thus, an expense to the business, it is typically cheaper than retaining a security team and toolset of the same caliber internally. Overall, MXDR usually has a lower total cost of operation to the business as realized through cost savings related to reduced complexity within the IT environment, shared licenses for software solutions, and valuable efficiencies unlocked for the IT team.
3. Increased visibility and control
MXDR provides complete, end-to-end visibility across the entire attack surface and consolidates all activity and insights within a centralized console. This provides the security team with a clearer, more complete view of threats and risks facing the organization; in addition, response and remediation capabilities, including the ability to automate some actions, grants organizations greater control over their security posture.
4. Resource optimization
The IT industry, and cybersecurity, in particular, is facing mounting talent shortages, which makes it difficult for even the most well-known companies to attract and retain the talent needed to organize and lead a security function. Further, determining how to respond to each alert as well as any active threat — and do so quickly before an intrusion becomes a serious breach — requires more manpower and expertise than is typically retained in-house.
As IT and security teams contend with staff shortages, increasing workload and the complexity of a widening toolset, MXDR is one way to help organizations simultaneously optimize staff and other resources and improve their security posture. This is especially important as companies increasingly lack the time or resources to fully deploy and optimize their existing solutions, as well as patch and upgrade applications and infrastructure. Utilizing an MXDR service to manage these tasks improves the overall security of the organization and also helps to reduce the workload of IT staff.
5. Improved threat detection
Finally, MXDR leverages the latest tools and leading minds within the cybersecurity landscape to protect clients from the most sophisticated threats. This ultimately translates into a stronger security posture for the business and enhanced protection for its customers.

Case Study: MXDR Protection Powered by CrowdStrike and Deloitte
Watch this case study to learn how the Dhanani Group, one of the world’s largest QSR franchise owners, partners with CrowdStrike to stay protected with MXDR.
Watch NowCrowdStrike’s MXDR solution
CrowdStrike Falcon® Complete XDR is the world’s first managed extended detection and response (MXDR) service with end-to-end remediation, from the #1 MDR leader.
Falcon Complete XDR provides 24/7 expert-driven management, proactive threat hunting, native threat intelligence, and end-to-end remediation across a customer’s entire attack surface to stop breaches. With native and third-party telemetry ingestion, organizations benefit from better cross-domain visibility and end-to-end remediation to eradicate threats holistically and efficiently.
Falcon Complete XDR expands its proven MDR service with added protection across more critical attack vectors. This enables rapid cross-domain detection of lateral movement and stealthy, advanced attacks.
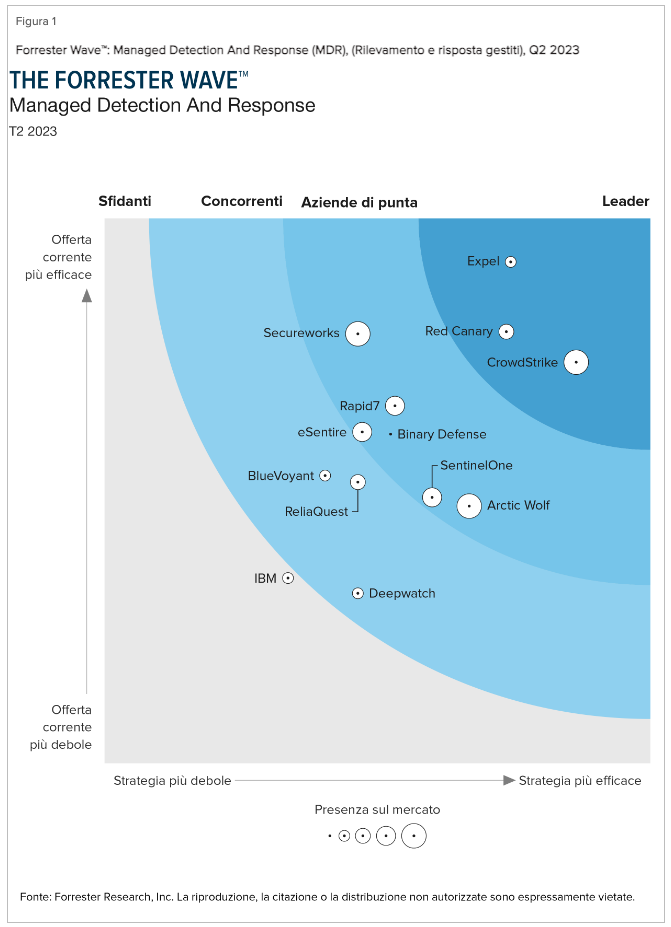
The Forrester Wave™: Managed Detection and Response, Q2 2023
Download the Forrester Wave™: Managed Detection and Response, Q2 2023 to learn how CrowdStrike sets itself apart and is named a leader in MDR.
Download Now

