CrowdStrike Cloud Infrastructure Entitlement Management (CIEM)

Introduction
The growing use of public cloud infrastructure not only expands the attack surface, but it also increases the management complexity and risk. Improper identity entitlement and overly-permissive accounts are factors in many cloud breaches. At CrowdStrike, Cloud Infrastructure Entitlement Management (CIEM) is a key part of cloud infrastructure security. Identity Analyzer helps you to identify crucial cloud account identity-related risks.
Video
Cloud Infrastructure Entitlement Management (CIEM)
CrowdStrike has developed policies for various cloud services that can be monitored and reported in the Falcon user interface. For each provider, the policies are listed including the default severity and policy type along with links to any relevant compliance information. There are options to enable the different policies and configure a custom severity for each registered cloud account.
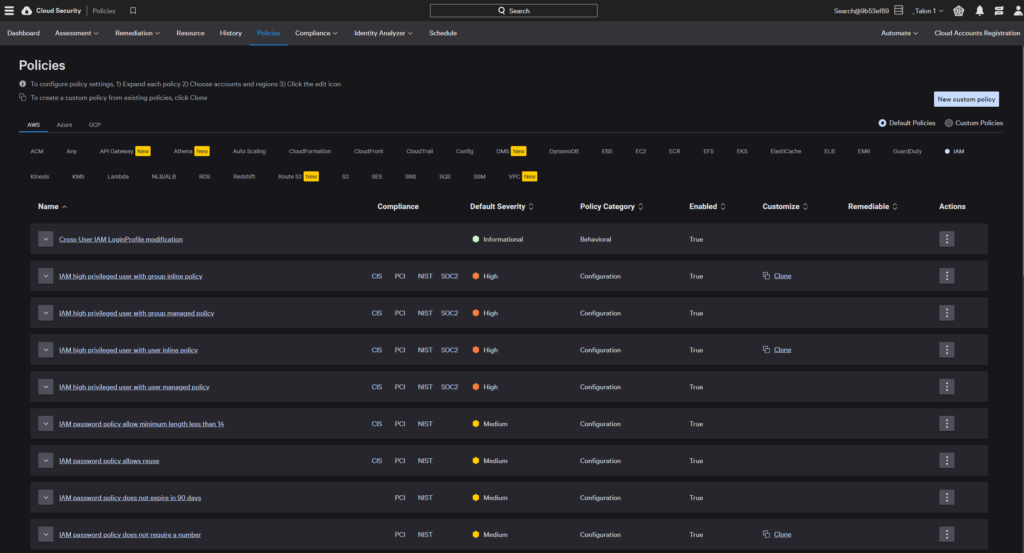
Looking at the AWS IAM, “Cross-User IAM LoginProfile modification” policy, we can see that it falls under the Persistence pattern of the MITRE ATT&CK Tactic.
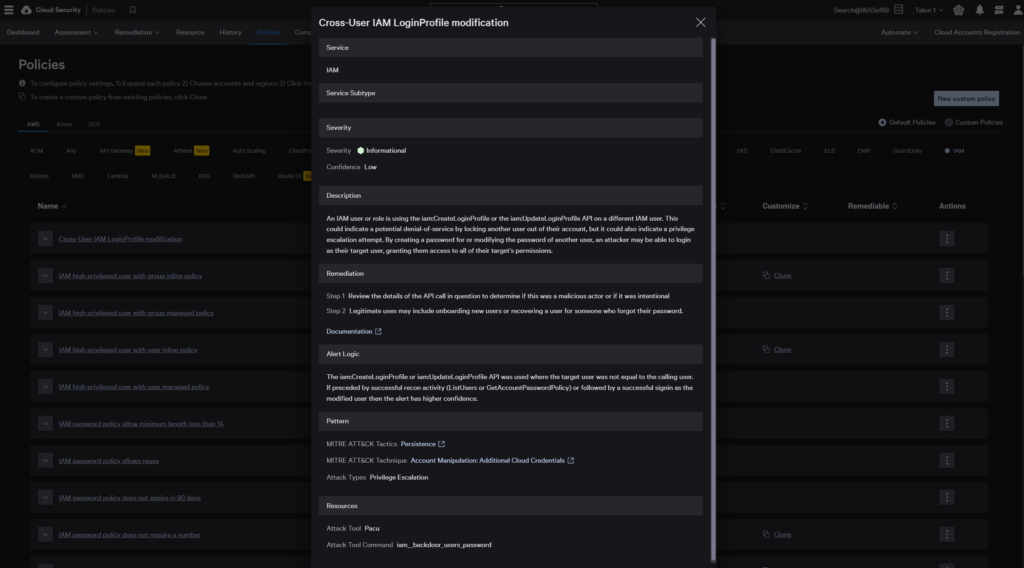
Under the Identity Analyzer, the CIEM dashboard illustrates an overview of recent findings across all of the registered cloud accounts and providers based on their MITRE ATT&CK pattern. Configuration related policies show up as Indicators of Misconfiguration and Behavioral policies show up under Indicators of Attack. This helps organizations to focus on the important Identity related threats.
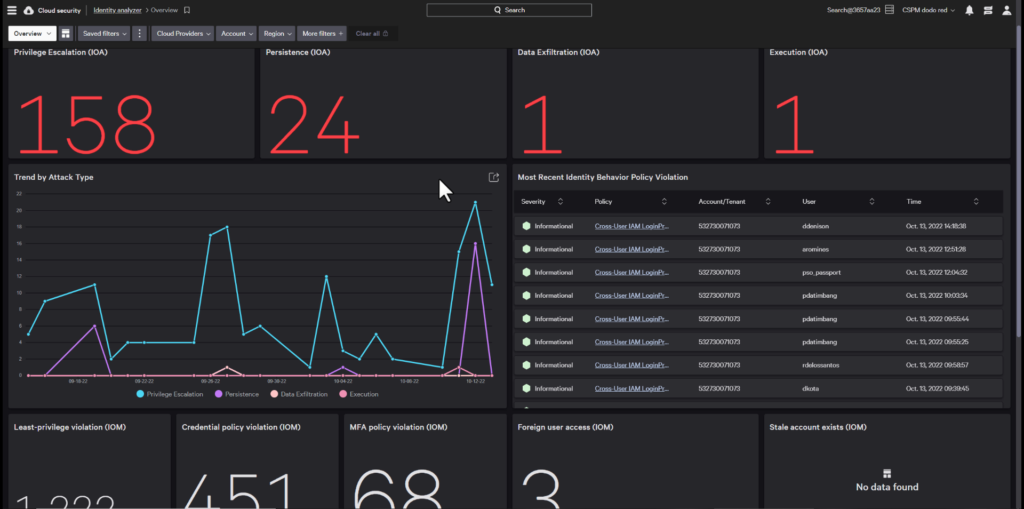
AWS Identity Analyzer
In addition to being able to assess different services and policies, CrowdStrike provides pre-configured dashboards for each cloud provider. You can use the Identity Analyzer to monitor AWS accounts for excessive or unused permissions, identify suspicious permission escalation, and audit AWS cloud services for actions allowed per resource, user, group, and role.
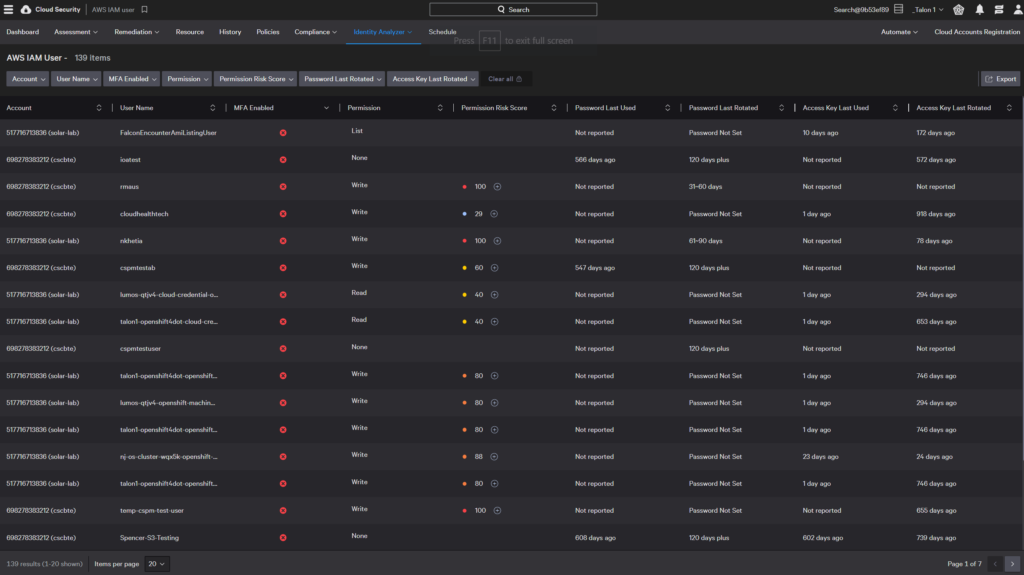
AWS IAM users
The AWS IAM User report can be filtered on username, multi-factor authentication status and permissions to quickly assess any compliance issues.
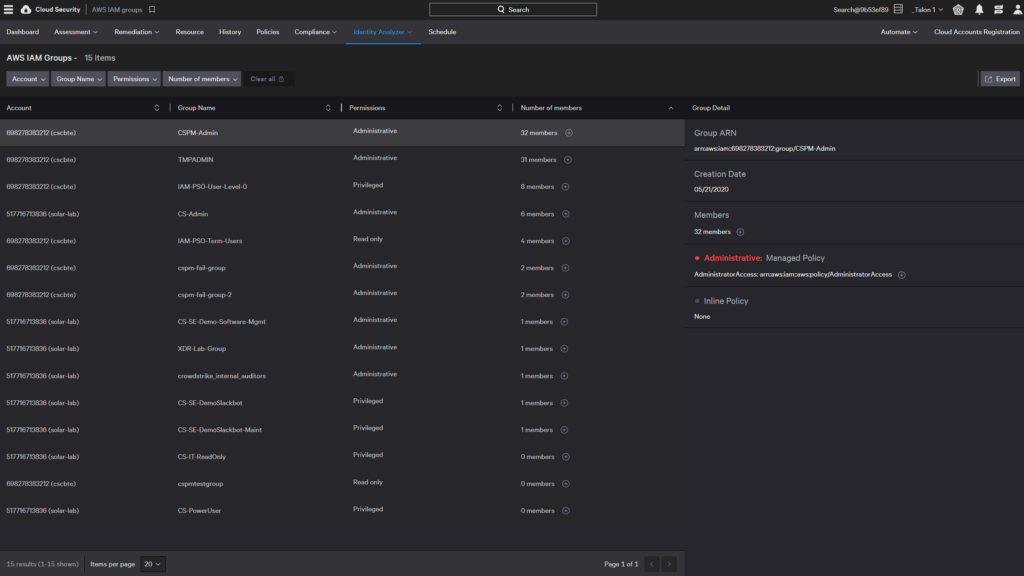
AWS IAM groups
An IAM group is a collection of IAM users. You can see AWS IAM group permissions, membership, and associated policies across all accounts in a single view. You can click the plus icons to see the membership list or the policy details.
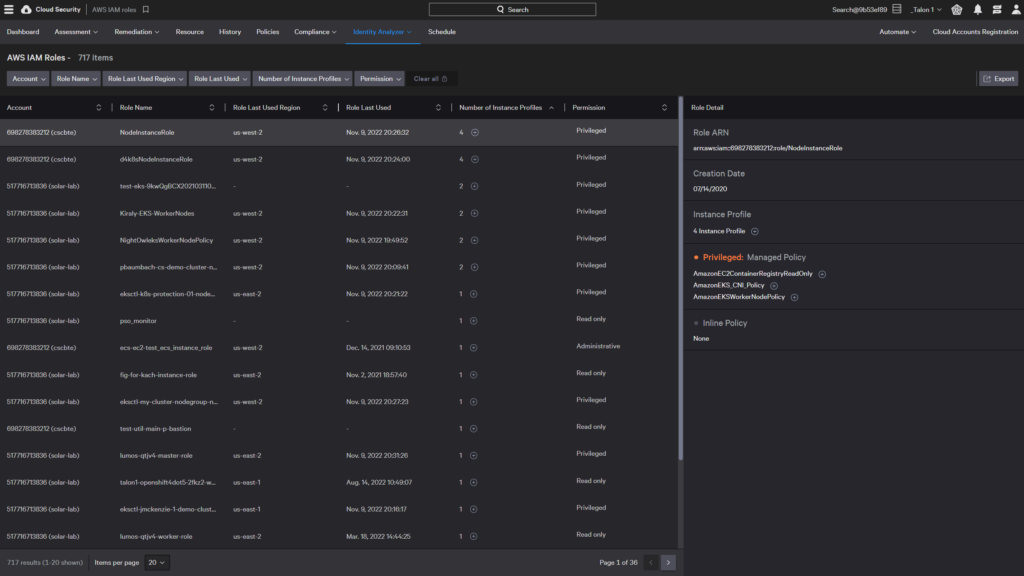
AWS IAM roles
An IAM role in an account has specific permissions. You can see AWS IAM role permissions, associated policies, and instance profiles across all accounts in a single view. You can click the plus icons to see the associated instance profiles or the policy details.
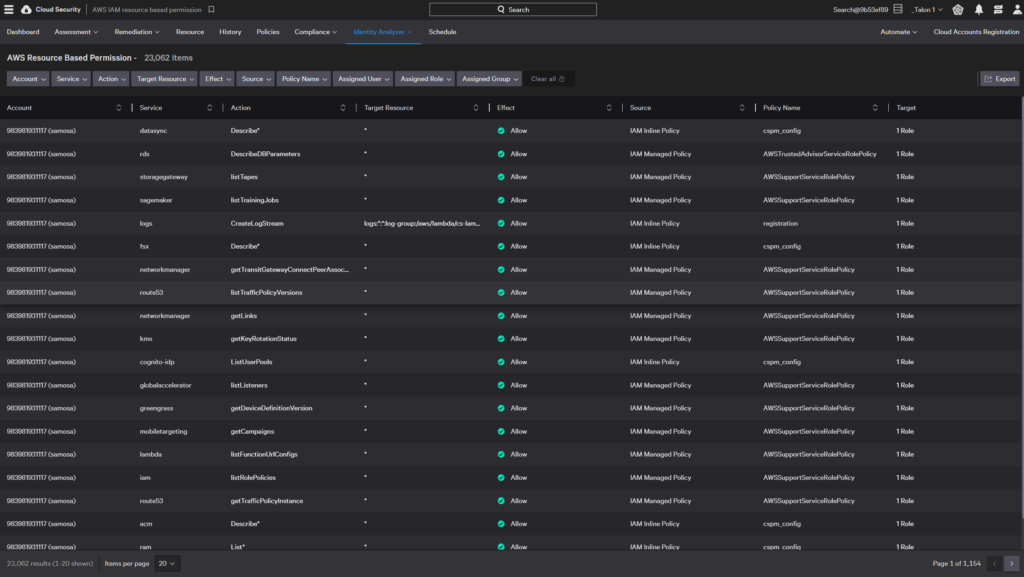
AWS resource-based permission
Resource-based policies specify who can access a resource and what actions they can perform on it. You can see the resources and permissions associated with an account.
Azure Identity Analyzer
You can get insights into your Azure AD configurations with Azure Identity Analyzer dashboards.
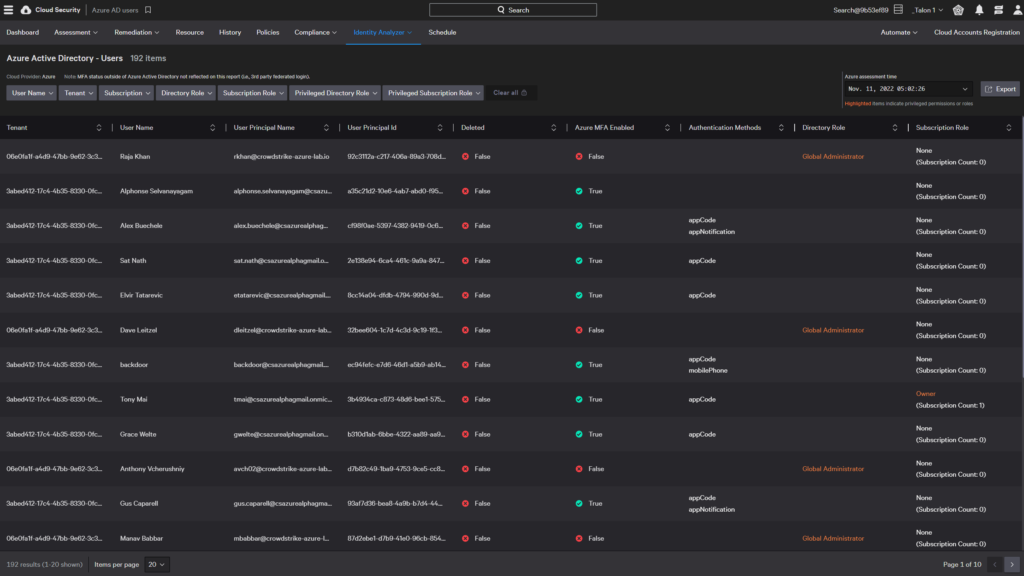
Azure AD users
The Azure AD Users dashboard displays all users created in your Active Directory with their assigned directory and subscription roles. You can use this dashboard to see users’ authentication methods, MFA status, high-privilege permissions.
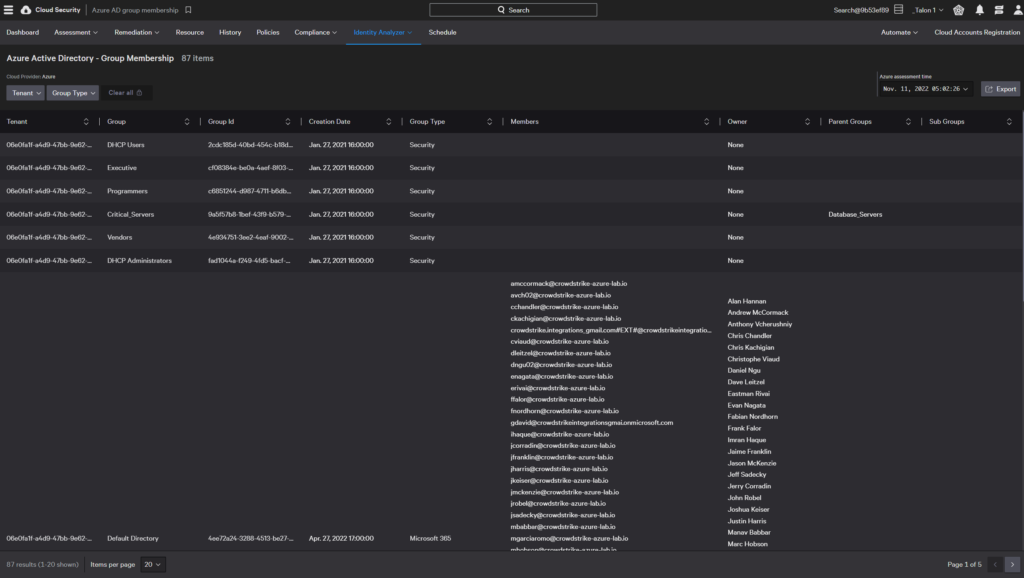
Azure AD group membership
The Azure AD Group Membership dashboard displays groups created in your Azure AD along with who owns the group.
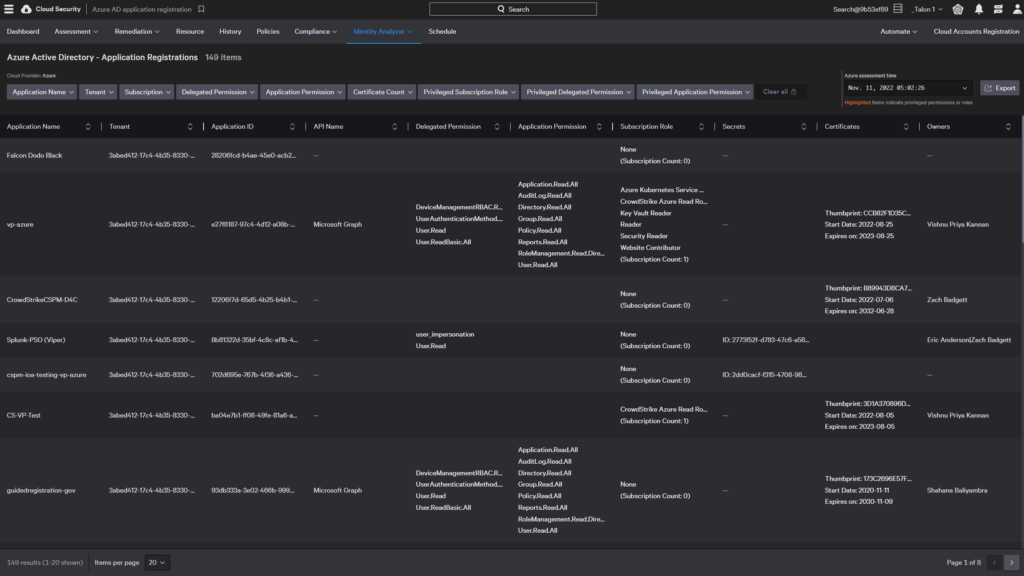
Azure AD application registration
The Azure AD Application Registration dashboard displays info about all Microsoft and third-party applications deployed to your Azure AD, along with their keys, credentials, and owner information.
The Crowdstrike CIEM solution applies the Principle of Least Privilege access to cloud infrastructure and services, helping organizations defend against data breaches, malicious attacks and other risks posed by excessive cloud permissions.